News
Inside the DigitalGlobe, GeoEye merger
Proposed combo gets anti-trust scrutiny
"They saw blood in the water and struck," said an industry executive.
The confidential email that landed at GeoEye’s Herndon, Va., headquarters in June looked like checkmate in the company’s unexpected competition for survival against DigitalGlobe, its rival in the U.S. satellite imaging market.
(more…)Secret apps by next week
The National Geospatial Intelligence-Agency plans to complete the process of installing app stores on all three intelligence networks when it opens the secret version within the next week. Unclassified and top secret versions are already open.
All NGA has to do now is figure out how to fill the stores with apps.
The agency has published about a hundred geospatial apps produced under individual contracts. NGA doesn’t think that approach is financially sustainable or the best way to take advantage of private sector innovation.
But how can NGA fire up the software industry to deliver apps on its own initiative?
That was the topic of an unclassified “Industry Day” held today at the William Allder Auditorium inside NGA’s futuristic Campus East facility in Springfield, Va.
The auditorium was filled almost to capacity by industry officials, some of whom asked hard-hitting questions about the shift NGA is attempting.
Until now, NGA has spelled out and paid for exactly the kind of software it required to solve specific geospatial problems. Under the app model, NGA will give companies broad categories of apps, such as “Counterterrorism” or “Transnational Analysis.” Developers would create apps on their own dime, submit them to NGA for security and legal approval, and earn returns based on how well the apps perform for users who download them from the stores. The apps could be downloaded to smartphones, tablets or desktops, subject to security rules.
“The best athlete will win,” said NGA’s Mark Riccio, application services director in the Online GEOINT Services Directorate, a group established by NGA in February.
NGA is still working out exactly how to measure performance and pay the app developers. Last month the agency released a request for information seeking ideas for compensation models.
The conundrum is that important apps might only be used by handfuls of users, which means numbers of downloads alone can’t be the reward metric. User feedback also would need to be considered, and so NGA is looking at systems of star-ratings and payments for apps that move from bronze to silver to gold categories.
Some fees would come from downloads, but at the industry day NGA officials did not spell out how those fees would be paid. A soldier in a Stryker vehicle, for example, could not whip out a credit card, one attendee noted after the session.
Once that issue is resolved, much would the apps cost to download? In the question and answer session, one of the attendees brought up the example of Angry Birds, the app store game with versions ranging from free to 99 cents.
Jill O’Connor, an NGA contracting lawyer, said prices would take into account how many users are likely to need the app. Some could cost $100, others $400 or even more.
“I don’t think we’re limiting ourselves to the 99 cents,” O’Connor said. “For the ones that only a handful of people will use – tens of thousands of dollars?” she said.
As far as timing, NGA has set bold goals. Director Letitia Long has told staff she wants 75 percent of all apps to come from the industry, not NGA, by July 2013.
NGA also wants developers to produce functional apps within 60 days from concept to operation. The agency is setting up a process to approve them for inclusion in the stores within two weeks of submission, which in the commercial world is about how long Apple requires to approve iPhone apps.
The case for laser links
Lots of factors need to fall into place if General Atomics Aeronautical Systems is going to use lasers to move imagery off its unmanned planes a thousand times faster than is possible with the radio communications used today.
The critical missing ingredient for the company’s proposed laser comm demos is a four letter word -- cash.
General Atomics is openly soliciting “government support” to turn its laser blueprint into hardware that could be tried out on unmanned Reaper planes. At this month’s Berlin Air Show, the company sought to help make the case by decloaking a teaming agreement it signed quietly months ago with the German company Tesat Spacecom, a laser comms pioneer.
The companies think they can use lasers to beam imagery from unmanned planes at a clip of about 2 gigabits per second, or “several hundred to a thousand” times faster than is possible with the radio frequency satellite links on the planes today, said Michael Perry, the General Atomics vice president for laser electro-optics.
If the companies can find a sponsor, one of their first steps would be to beam imagery from an unmanned Reaper to a satellite in low Earth orbit. Ultimately, though, they want to send the laser 22,500 miles into space to a communications satellite called Alphasat. It is scheduled for launch in 2013 to a position over Europe, Africa and the Middle East for the European Space Agency and mobile communications giant Inmarsat. Alphasat’s main job will be to serve Inmarsat’s BGAN mobile comms customers, but it also will carry unrelated, or hosted, payloads. One of these happens to be a demonstration laser communication terminal built by Tesat.
If the demo goes as planned, the Reaper imagery would arrive by laser at the Tesat terminal, but it would be relayed to ground sites via multiple ka-band radio frequency transmissions.
General Atomics engineers are not the first experts to think about using lasers for faster communications. Lots of research has been conducted by DARPA and the Air Force Research Lab, but General Atomics wants to tie the technologies into a new application: “To our knowledge, this would be the first laser comm capability on a UAV,” Perry said.
If it works, flight crews in ground control stations in the U.S. would be able to view more terrain on their screens, and so would intelligence analysts at fusion sites.
General Atomics hasn’t said which agencies it is pitching the demos to, but Pentagon officials fret about the readiness of networks and communications links to handle imagery from new multi-camera wide area surveillance systems that take city-sized snapshots several times a second. Reapers carry the Gorgon Stare wide area imaging pods. They will probably end up carrying the even wider area Argus-IS systems in development by BAE Systems as the next version of the Gorgon Stare imaging system provided by Sierra Nevada Corp.
Most unmanned planes are still equipped with full motion video cameras that deliver soda-straw views just meters across.
For General Atomics, some factors have fallen into place toward the laser demos. The company has received permission from the State Department to share data and expertise with Tesat, Perry said. That makes it possible for the companies to collaborate on building hardware. The companies are refining their blueprint now that they are free to talk. If a sponsor is found, most of the equipment would be built by General Atomics; Tesat would provide some critical components.
The biggest technical challenge will be squeezing the communications package into a housing small enough to ride on the aircraft’s fuselage without disrupting its aerodynamics.
The company has tested the laser housing on a Reaper with good results, Perry said. “The main purpose of the experiment was to show it was aerodynamically stable and did not have a negative impact on the endurance – and both those things were shown,” he said.
The remaining work should be doable.
“What we’re talking about is something that is a derivative of systems that Tesat has done in the past,” he said. “This is not [about] looking for some kind of fundamental breakthrough at this point.”
Air Force explains automation delay
A popular metaphor in Air Force intelligence circles has analysts drowning in a sea of data. To hear the service's intelligence chief tell it, the service now risks drowning in something else: A sea of proposals for how to handle the video and signals intelligence beamed down by 57 unmanned aircraft patrols and round-the-clock flights by MC-12 Liberty turboprops.
Air Force Lt. Gen. Larry James defended the methodical preparations the service has been making toward automating aspects of its notoriously labor-intensive processing, exploitation and dissemination, or PED, chain.
The Air Force Research Lab has been assigned to act as a "filter because frankly there are a lot of people out there with ideas for a product which may or may not work," James told an audience at the Air Force Association conference in Maryland.
Industry officials, including at least one in the conference audience, are growing frustrated that the service's top generals began publicly calling for automated tools more than a year ago but have yet to match those calls with a process for setting requirements and funding purchases of the tools.
James said an experimental processing system has been set up at an AFRL site so "we can actually take those tools and operate them on the system, with an analyst in the loop, and understand, 'Is this something that's worthy for us to invest in?'"
An adequate science and technology and rapid acquisition process is now in place, James said. Meeting with reporters later, he added that a "roadmap" for purchasing the tools would be established by the intelligence surveillance and reconnaissance review that's been underway for about a year and a half for Air Force Secretary Michael Donley.
"That should be done by the end of the year. Then we'll have a pretty good idea, of, 'Okay this is where we need to be in 2015, this is where we think we'll be in 2018,'" he said.
James made clear that even as the U.S. prepares to hand over the lead to Afghan forces, the service expects to collect more and more video and signals intelligence over Afghanistan and other hotspots.
The Air Force has been holding steady at 57 combat air patrols of Predator and Reaper planes over Afghanistan and "other parts of the Mideast," he said. The pause in growth was necessary: "We've been in the middle of reconstituting our training program, reconstituting our weapons school," he explained.
In November, the holding pattern will end, and the service will begin adding patrols to reach about 65 by May 2014, and "ultimately the capability to surge to 85 combat air patrols."
It's not just the number of patrols that's creating the desire for automation, James said. A big driver will be a next generation version of the Gorgon Stare wide area camera system called ARGUS-IS, short for Autonomous Real-Time Ground Ubiquitous Surveillance-Imaging System.
"The data content and size is not slowing down," James said.
Big data is not always easy to work with either. James said the service has had technical trouble moving Gorgon Stare wide-area motion imagery from location to location, but that he thinks the Defense Information Systems Agency has solved the problem.
Aerostats as swarming boat spotters
A time honored strategy for reinvigorating a defense project in Congress is to tie it to an issue on the minds of lawmakers.
That's Raytheon's strategy for saving its radar-equipped JLENS aerostats, known formally as Joint Land Attack Cruise Missile Defense Elevated Netted Sensor systems.
Unless Congress or the Pentagon's acquisition chief steps in, the Army will wrap up all of its JLENS work in 2014, aside from a possible "Combatant Command Exercise" somewhere in the U.S. before 2017. Even that exercise looks problematic, with Senate appropriators balking at paying $30.5 million in 2013 toward it. The project could end with just four aerostats, no real world test and $2 billion expended.
Raytheon hasn't given up hope for continuing into production with JLENS, which is where the issue on the minds of lawmakers comes in.
As the term "cruise missile" in the name suggests, the Army kicked off the JLENS project in 2006 mainly to show how radars could stare down from aerostats and track terrain-hugging missiles, helicopters and small planes.
With lawmakers flocking back to town and tensions simmering with Iran, Raytheon is pointing to JLENS as part of the answer to the worry that small boats could swarm around U.S. warships, particularly at strategic choke points.
If you were to guess that means the Strait of Hormuz, Mark Rose's eyes will widen and you'll be pretty sure you detect a nod. Rose, a 32-year Raytheon employee, directs the company's JLENS work.
"Swarming boats have been in the plan all along, but it's receiving more urgency now given the threat sets in the world," he tells Deep Dive.
In June, Raytheon laid the groundwork for the case by motoring two small inflatable boats over Utah's Great Salt Lake. It wasn't a swarm, but it was good enough to test JLENS' ability to track small boats in motion. JLENS has tracked large numbers of cars on distant highways, which makes Raytheon confident the aerostats can handle lots of boats too.
Swarm conjures images of boats racing toward U.S. ships, but actually the bigger challenge for a Doppler radar is to track slow moving things. JLENS did better than specifications when engineers tested how slowly they could move the boats and still keep track of them, an Army official says.
At the moment, there are no plans to send JLENS to any distant hot spots, which is not to say that hasn't been considered. There was a plan to send JLENS to someplace in the Central Command area but the idea was shelved more than a year ago out of concern that the deployment could be seen as provocative.
"It's a pretty big step when you put a football field-length airship up in that region," the Army official says.
In Congress, Raytheon could be onto something with its new focus on swarming boats. House authorizers, for instance, want the Navy to field a 100 to 200 kilowatt laser to defend ships against drones, cruise missiles and also "fast attack craft threats."
"The beauty of this system is that you can see things from so far away that you have lots of time to make decisions," Rose says. Plus, by flying for 30 days at a time, JLENS could also map patterns of life on land and sea, he adds.
Each system consists of two, 74-meter-long aerostats. One is equipped with a VHF-radar for surveillance. The other carries an X-band fire control radar for locking weapons onto targets. The radar readings are sent to the ground via fiber optic cables protected inside each aerostat's Kevlar-reinforced tether. Operators feed them into networks, including the Navy's Cooperative Engagement Capability network.
JLENS is designed to detect and track small aircraft, boats or trucks out to a range of 512 kilometers.
Rose says that if he had his druthers, the Pentagon would send a JLENS to a location where it could track objects both on land and at sea. Ultimately, Raytheon hopes the Pentagon will reverse course and issue a production contract.
If that happens, JLENS will have bucked a troubled history. In December 2010, the Pentagon reported that its unit cost had risen 17.88 percent, which amounted to a "significant breach" of the Nunn-McCurdy cost control law. One factor was bad luck. In September, a JLENS was riding out a tropical storm on the ground in Elizabeth City, N.C., when another aerostat crashed into it, seriously injuring a worker and damaging the JLENS beyond repair. Elizabeth City is the manufacturing hub of TCOM, the lighter-than-air specialists who made the JLENS hulls for Raytheon.
Bad luck, shifting Army priorities and radar development delays prompted the Pentagon to scrap plans to purchase 16 JLENS systems. The decision left just the two systems now in the inventory, which equates to four aerostats. The reduced buy sent projected unit costs upwards and triggered a full-on Nunn-McCurdy breach that required the Pentagon to recertify the program to Congress. The recertification has had limited impact so far. The Pentagon continues to plan for the exercise but has no plans at the moment to procure more of the aerostats.
Rose says Raytheon has figured out how to cut production costs by incorporating components from the company's contributions to the anti-missile Terminal High Altitude Area Defense system, or THAAD, which spots missiles and knocks them down high in the atmosphere. "We've been able to reduce the cost 30 percent by recognizing the commonalities," Rose says. The strategy allows Raytheon to negotiate higher volume purchasing agreements with component suppliers.
Interview: At the center of the IT revolution
Mike Mestrovich is DIA's senior technology officer for solutions in the information management directorate. Think of him as the agency's advanced IT guru. In past lives, he's helped build nuclear targeting tools for the Air Force and worked on government networks for Cisco. Depending how things go, the highlight of his career could be the role he was assigned earlier this year as chief architect for a key element of the intelligence community's IT efficiency drive. Mestrovich leads the team that's designing a common desktop computing environment for workers across the agencies. He spoke to Ben Iannotta about the desktop, the apps craze and the feasibility of going mobile.
Read excerpts below >>
 Intelligence Community Information Technology Enterprise (ICITE, pronounced eyesight)>> It'll create "a common desktop to all IC members, such that any IC person could go to any IC desktop, log in and have access to their emails, their files, their sharePoints, all of that stuff…It's certainly a consolidation event and an efficiencies event and something that's never been done before. It's a huge deal. It's a big game changer for the intelligence community."
Intelligence Community Information Technology Enterprise (ICITE, pronounced eyesight)>> It'll create "a common desktop to all IC members, such that any IC person could go to any IC desktop, log in and have access to their emails, their files, their sharePoints, all of that stuff…It's certainly a consolidation event and an efficiencies event and something that's never been done before. It's a huge deal. It's a big game changer for the intelligence community."
ICITE schedule >> "There's tens of thousands of people in the intelligence community … the expectation is that on -- around the 31st of [March] next near – indeed some of those people, the early adopters if you will, will have a common desktop…"
FBI, Treasury, DEA too?>> "All of those are scheduled to be included in the ICITE activity. There's a phased implementation and we're right now looking at when do we start bringing in those other agencies."
Latest on ICITE >> "NSA and CIA were designated as the cloud service providers. DIA and NGA jointly were designated as the desktop service provider. There was an Applications Mall service provider, and then individual app stores would be delivered by individual agencies. We've just gone through some design reviews for that… And we're now in effectively the implementation phase of that…"
Real world mobility >> "It's one thing to be sitting hopefully with nobody around you, reading secret emails…It would be a totally different thing to be actually having an open, verbal classified conversation….the capabilities certainly continue to advance and give us the opportunity to do that. You just have to be cautious of, you know, when is the most appropriate time to engage in that activity?"
Connected in your SCIF (sensitive compartmented information facility) >> "Inside the classified space, we certainly want to enable people to have more mobility than they had. So, ideally, we'd love to have the environment where you do pick up your laptop and go to the meeting room and your laptop is capable of connecting wirelessly and processing TS information. That is something we are striving towards. Lot of work to do in that space, but it's something we're going towards."
Apps Mall >> "There's lots of operational activity behind that. How do I know that you as a person have the need to know?....How are you trained to run the application? There's a lot of different operational components behind it, but natively what was understood was there would be kind of a central repository where all the analysts could go, much like you do with your iPhone or Android device today. You get an opportunity to search and see all the apps that are out there. And maybe you discover that there's some new ones and you try them out and you find that they do have some applicability…"
Evolution >> Historically, the director for information management had what they called senior account managers….The process has evolved a little bit…We have something where the customers actually get together amongst themselves in the functional disciplines, and they themselves kind of vet out requirements. We don't get effectively conflicting requirements, or diametrically opposed requirements - You know, PaCom wants you to do X, and EuCom wants you to do Y, and X and Y are totally incompatible with one another."
Talking stops, work starts on network consolidation
After a year of planning, the intelligence community has started the vast information technology project that the community is counting on to prevent deep cuts to collections and analysis in future years.
Mike Mestrovich, DIA's senior technology officer for IT solutions, says the shift from talking to doing was made in mid August.
"We're now in effectively the implementation phase," he tells Deep Dive. "Service providers are now building out the various different components of that IT architecture, with an expected IOC [initial operating capability] date for the IT enterprise of the 31st of March 2013."
He's referring to development of the Intelligence Community Information Technology Enterprise, or ICITE (say eyesight).
Earlier this year, the intel agencies reached agreements about who would do what under the effort, whose basic outline and goals are unclassified.
CIA and NSA – two of the service providers referenced by Mestrovich – will shift information from fixed data centers into data storage clouds. DIA and the National Geospatial-Intelligence Agency are working jointly on a common desktop operating system for intelligence workers to be rolled out in phases. Mestrovich is chief architect for it. NSA is creating an Apps Mall that will incorporate apps stores of the various agencies.
No public dollar figure has been put on these changes, but they are supposed to generate enough savings later to prevent cuts to collections and analysis as the community throttles back its overall spending over the next decade.
An app for secure phone comms
On site with TeleCommunication Systems
The first thing you notice in the foyer of the TeleCommunication Systems headquarters in Annapolis is the flat screen TV with red dots showing where people in the U.S. are making 9-1-1 calls on their cellphones.
The locations are calculated with technology from TCS and other companies that provide Enhanced 9-1-1 services to Verizon, AT&T and other carriers. The display zooms in on one of the dots, and I'm a little spooked when I recognize the street name. It’s around the corner from my favorite Maryland fishing shop.
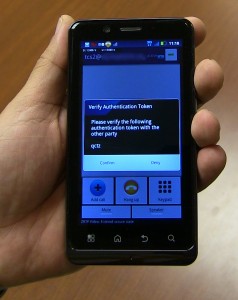
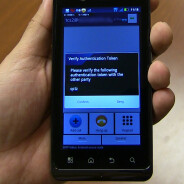
Authentication tokens will ensure you're not being spied on when using TeleCommunication Systems' new app. Credit: TCS
TCS operates at our society's convergence of military, intelligence and civil technologies. One moment it's helping 9-1-1 operators find wireless callers. The next it's transmitting text messages for consumers - 900 billion in the past 12 months. It also runs an unclassified "Art of Exploitation" cyber training course, and it has big plans to win a place in the network protection business.
TCS was founded in 1987 by Maurice B. Tosé. He's an Annapolis-grad and Naval reserve officer who remains CEO, president and chairman. Tosé is African American and he started the company with the aid of section 8(a) of the Small Business Act. It gives an edge to minority-owned small companies for some federal contracts. TCS started out by providing satellite communications to special operations forces, but the company has diversified and grown to 1,400 employees. It does not plan to stop there.
None of that is why TCS executives invited me here to their headquarters on the fourth floor of a brick office building in Annapolis. They want me to try the new secure wireless phone service they're developing.
TCS is one of the firms chasing a potentially lucrative line of business sparked by the National Security Agency. NSA has started a Mobility Program whose goal is to give government workers "the rich user experience of commercial technology" even when they're engaged in secure communications.
The underlying technology sounds hard to believe. NSA wants companies like TCS to figure out how to carve secure communications tunnels through commercial 3G and 4G networks using multiple encryption layers and authentication protocols. Government workers would download the apps onto phones of their choosing – or maybe their agency's choosing – under an approach dubbed BYOD for Bring Your Own Device.
TCS likes to point out that its version requires no extra hardware. Workers would simply download the app through one of the new government app stores now in the works.
NSA has been testing the basic concept of secure mobility under a pilot project called Project Fish Bowl – the bowl being encryption and authentication, and the fish being government workers. NSA would judge the security of the services but individual agencies would do their own selecting.
I don't have good insight yet about whether Fish Bowl is gaining traction, but TCS sure acts like it is. The company has soaked up every nuance it can find in the series of "Mobility Capability Packages" NSA began publishing on its public website in February. These guidelines tell competitors like TCS how to structure their secure communications services.
TCS expects NSA to release its last package before the end of the year, and hopes to start selling its service in 2013.
For now, though, I'm intrigued to have one of their demo phones in my hand. It happens to be a Motorola but really it's the app that matters. Across the conference room table, TCS' Vineet Sachdev holds an identical phone.
Sachdev is director of product marketing and management. He enters a password for me so that a TCS computer called the Security Broker can wirelessly verify it. The broker also generates the cryptographic keys that will scramble our voices on one end and de-encrypt them on the other. When Sachdev and I begin our conversation, a string of four authentication characters, called a token, appears on each of our screens. The first thing the participants in a secure call would do is read their tokens to each other. The characters are supposed to match. That's how the system verifies that a Voice Over Internet Protocol call is not passing through a "man-in-the middle" computer, a device programmed to eavesdrop. Sachdev says he won't reveal exactly how the authentication works, but in a nutshell, the two devices pass content between each, and this content would generate mismatching characters if it had passed through a third computer.
After we verify that our tokens match, I touch confirm.
Our voices are traveling over the Verizon consumer network, but the signals are disguised by the government's Advanced Encryption Standard 256 algorithm.
This was fun, but I wouldn't dare try to weigh the security merits of the TCS system. That said, the phone looks and feels familiar. It's easy to see why some people want this type of secure communications to be the future.
Interview: The End of Kumbaya?
As Chairman of the House Permanent Select Committee on Intelligence, Rep. Mike Rogers, R-Mich., has restored a measure of bipartisanship to a committee that was deeply divided by the George W. Bush years. The former FBI special agent faces the task of keeping the good will flowing even as he criticizes the Obama administration's handling of classified information and the adequacy of its intelligence approach to Syria. Rogers spoke with Ben Iannotta in his Capitol Hill office.
Read excerpts below >>
 On Bipartisanship >> "I've tried to take all the edges out of the national security debate.…Working with Democrats on my committee and take their suggestions, their offers, their amendments before it gets to the place where you're supposed to fight about things, so that we can have an honest debate about it."
On Bipartisanship >> "I've tried to take all the edges out of the national security debate.…Working with Democrats on my committee and take their suggestions, their offers, their amendments before it gets to the place where you're supposed to fight about things, so that we can have an honest debate about it."
Oversight of the IC >> "When they're wrong, we need to tell them they're wrong. When they're right we should not be bashful about telling them they're right."
Political linkage >> "In this line of work, people do understand we're going to have differences of opinion. That's why you have Republicans and that's why you have Democrats….I'm out trying to repeal Obamacare today but we're working on very sensitive national security issues together the next day."
Polygraphs >> "There needs to be more than that. I would argue that there has to be some moral leadership coming out of the White House as well [to plug leaks]…There's a whole nother group of individuals that won't fall under those rules…National Security Council individuals and staff, and the folks who deal with that that come into a presidency and leave with a presidency."
Whistleblowers >> "When it comes to classified information, you cannot have individuals determining by what small piece of the world they see what should and should not be classified. That is a recipe for disaster. And there are lots of outlets. We have a Whistleblower Protection [Act] for a reason. They can come to a committee like the intelligence committee and offer up classified, sensitive information. It happens by the way, and we take every case that comes into our offices extremely seriously."
Syria collection strategy >> " I think being slow on an event like this is just not helpful… sometimes we just don't get to pick on our calendar when things happen, but we have to be willing to make hard, quick decisions to make sure we stay ahead of it. And I'm not talking about doing any action. I'm just talking about putting the United States government in a position to collect information that policy makers need to make good decisions. We're not just there yet."
Syrian rebels >> "There's been a lot of calls for arming rebels and I have been opposed to that because I just don't believe we know enough…As a policy maker, when you're talking about arming individuals to overthrow a government that's a big deal. It should be a big deal."
Analysts and agents >> "You take a counter terrorism case, and as complicated as they are, an analyst is critical to a better conclusion quicker… An analyst can help bring in information from across the country. The Crowley [sic: Coleen Rowley] case is a great example of that. If there had been an analyst on that case, who knows?"
Fort Hood intelligence >> "Somebody thought information was sensitive and not for sharing because of the way it was collected, and it was really just a simple mistake…And there was clearly some indications that the Army was very reluctant to move forward. They thought that they would be punished for being maybe overly aggressive with someone based on their religious beliefs…As an investigator, you can never do that…You have to take your leads where they take you."
Fort Hood confusion >> "It can be fixed…You had two very different cultures [in the Fort Hood case] trying to work in the same room "
Privacy >> "If you're an average citizen, the government isn't willy nilly collecting it and sitting down and having a good laugh over your emails and your tweets. It's not happening. In order for them to access your information, they have to have a warrant in order to say, 'Hey, I'm going to look at Mike Rogers' emails for the next three months,' They have to go to a judge and prove that there is some reasonable belief that there is going to be a crime committed."
Cybersecurity legislation >> " If we can get something that isn't overly proscriptive, overly regulatory to a conference committee, I think we can probably work out details to get something to the president…this fall.
FISA renewal >> "I think there's a difference between a big fight and a scuffle. I think you're going to see a scuffle."
IT modernization >> "If you're sitting at a desk having five different systems, we just can't sustain that any more. So we're going to have some merger of IT and some consolidation and synergy of services when it comes to IT."
Cloud security >> "We're still working through the security protocols to make sure that this stuff is safe and secure, not accessible outside of the cloud itself, so that you don't have intrusions that are dangerous to national security. We have all of that to work through. But I do think we're probably going to have to get there. I think it's the wave of the future."
General Dynamics makes addition to threat intel business
The planned General Dynamics purchase of Fidelis Security Systems might look like a case of a giant buying a cyber upstart to reduce competition, but executives said that is not what's happening here.
"This is really not about swallowing Fidelis, this is about giving it some resources to enable it to grow," said GD's John Jolly.
The companies announced an agreement Aug. 20 to purchase Fidelis at a price they are not yet revealing. Executives said the deal is 99.99 percent likely to be finalized.
Once that happens, the 70-employee company will be called GD Fidelis Security Systems and it will retain its offices in Bethesda, Md., and Waltham, Mass. "We are not planning any personnel moves as part of this," Jolly said.
Jolly and Fidelis President CEO Peter George discussed the acquisition in a telephone interview with Deep Dive.
Experts from General Dynamics already work closely with the intelligence community to respond to network threats and produce intelligence. What GD does not have is malware-detection software to sell along with those services.
That's where Fidelis will come in. The company's software inspects network traffic for evidence of malware and then blocks attempts by hackers to communicate with their handy work via network ports.
"When a bad guy wants to exfiltrate classified information, we can see that going outbound and do something about it," George said.
Depending on how things go in Congress, the timing of the acquisition could be fortuitous for GD. The company does not publicly take sides on pending legislation, but a cybersecurity bill introduced by Sen. Joseph Lieberman, I-Conn., would provide incentives for private companies to buy exactly the kind of software made by Fidelis.
Not surprisingly, Fidelis has been a strong supporter of S.3414, the Cybersecurity Act of 2012. "Having nation states steal our intellectual property is a national security issue," George said.
On Aug. 2, the Senate fell short of the 60 votes necessary to move the legislation forward to a final vote, but George said he hopes the Senate will revive the proposal after the presidential election.